Building a Password Game: A Comprehensive Guide to Engaging and Educational Entertainment
Related Articles: Building a Password Game: A Comprehensive Guide to Engaging and Educational Entertainment
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to Building a Password Game: A Comprehensive Guide to Engaging and Educational Entertainment. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Building a Password Game: A Comprehensive Guide to Engaging and Educational Entertainment
The creation of a password game presents an intriguing opportunity to blend entertainment with educational value. This type of game encourages players to develop critical thinking skills, enhance their understanding of security principles, and foster a sense of accomplishment through successful code-breaking. By delving into the intricacies of game design, programming, and security concepts, this article provides a comprehensive guide to building a password game that is both engaging and educational.
Conceptualizing the Game:
The first step in building a password game is to define its core concept and objectives. This involves identifying the target audience, determining the desired learning outcomes, and establishing the overall game mechanics.
1. Target Audience and Learning Objectives:
- Target Audience: Identifying the intended players is crucial for tailoring the game’s complexity and content. Are you targeting children, teenagers, or adults? What are their existing knowledge levels regarding security and passwords?
- Learning Objectives: What specific skills or concepts do you aim to teach? Do you want to emphasize password strength, security best practices, or the fundamentals of cryptography?
2. Game Mechanics:
- Gameplay Style: Will the game be a single-player or multiplayer experience? Will players be required to crack passwords, create strong passwords, or both?
- Game Setting and Theme: Choosing a compelling setting and theme can enhance player engagement. Consider themes like espionage, hacking, or fantasy worlds.
- Difficulty Levels: Incorporating difficulty levels allows players to progress gradually, ensuring a satisfying challenge without overwhelming them.
3. Password Generation and Validation:
- Password Generation: The game should provide a mechanism for generating random passwords or allowing players to create their own. This requires a secure and robust password generation algorithm.
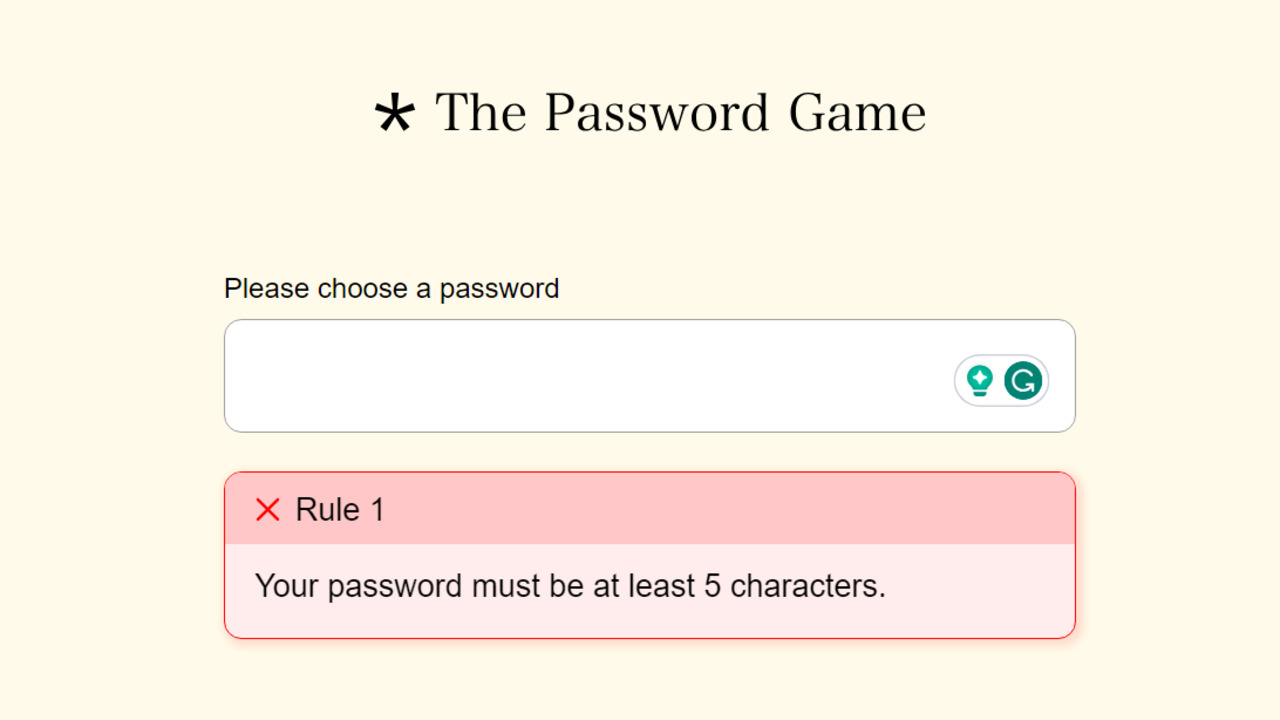
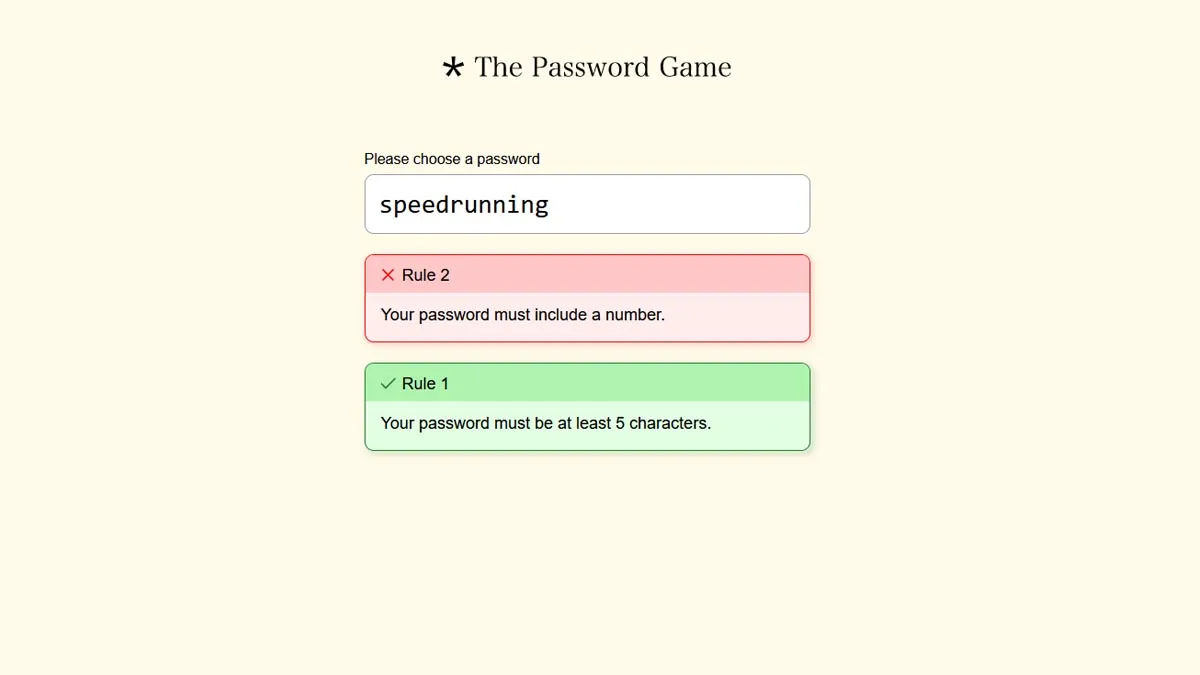
- Password Validation: The game needs to validate user-generated passwords against established security criteria. This can include checking for length, character diversity, and the absence of common patterns.
4. Game Interface and User Experience:
- Visual Design: A visually appealing and user-friendly interface is essential for player engagement. Consider using clear graphics, intuitive controls, and engaging sound effects.
- User Feedback: Provide clear and constructive feedback to players, indicating their progress and highlighting areas for improvement. This could include hints, tips, or score displays.
Technical Implementation:
Once the game concept is finalized, the next step is to translate it into a functional game using programming languages and development tools.
1. Programming Language Selection:
- Python: Python is a popular choice for game development due to its simplicity, readability, and extensive libraries.
- JavaScript: JavaScript is commonly used for web-based games, offering interactive elements and client-side functionality.
- C++: C++ provides performance and control over system resources, making it suitable for complex and resource-intensive games.
2. Game Development Tools:
- Unity: A cross-platform game engine with a user-friendly interface and comprehensive features.
- Unreal Engine: A powerful engine known for its high-quality graphics and advanced features.
- GameMaker Studio: A user-friendly engine suitable for both beginners and experienced developers.
3. Password Encryption and Security:
- Hashing: Using secure hashing algorithms like SHA-256 or bcrypt to store passwords securely.
- Salting: Adding a random salt value to each password before hashing to enhance security.
- Password Complexity Rules: Implementing rules for password complexity, such as minimum length, character diversity, and the avoidance of common patterns.
4. Game Logic and Mechanics:
- Password Cracking Mechanisms: Implementing algorithms for password cracking, such as brute force, dictionary attacks, or rule-based cracking.
- Game Difficulty Levels: Implementing logic to adjust the difficulty of password cracking based on player progress or chosen settings.
- Scoring and Achievements: Designing a scoring system and unlocking achievements to incentivize players and track their progress.
Examples of Password Games:
- Cybersecurity Education Games: These games often involve scenarios where players need to crack passwords to access systems or information, highlighting the importance of strong passwords and security best practices.
- Code-Breaking Games: Games like "Enigma" or "The Code" challenge players to decipher encrypted messages, fostering an understanding of cryptography and code-breaking techniques.
- Logic Puzzles: Some games incorporate password elements as part of a larger puzzle, requiring players to solve logical problems to unlock clues or progress through the game.
FAQs about Building a Password Game:
1. What are the benefits of creating a password game?
Creating a password game offers several benefits, including:
- Educational Value: It can teach players about password security, cryptography, and the importance of strong passwords.
- Engagement and Fun: It can make learning about security more engaging and entertaining.
- Skill Development: It can help players develop critical thinking, problem-solving, and logical reasoning skills.
2. How can I ensure my game is secure?
To ensure your game is secure, you should:
- Use strong encryption: Employ robust hashing algorithms and salting techniques to protect passwords.
- Implement password complexity rules: Encourage players to use strong passwords that meet minimum length and character diversity requirements.
- Protect sensitive information: Store passwords securely and avoid exposing them to unauthorized access.
3. What are some tips for designing an engaging password game?
- Clear objectives: Define clear goals and objectives for players to understand their purpose in the game.
- Variety of challenges: Offer a range of challenges and difficulty levels to keep players engaged.
- Reward system: Implement a rewarding system with scores, achievements, and incentives to motivate players.
- Visual appeal: Use appealing graphics, sound effects, and animations to enhance the user experience.
Conclusion:
Building a password game presents a unique opportunity to combine entertainment with education. By carefully considering the target audience, learning objectives, game mechanics, and technical implementation, developers can create engaging and educational games that promote awareness of password security and foster a sense of accomplishment in players. The key is to strike a balance between challenge and reward, ensuring that the game is both stimulating and enjoyable for all players.






Closure
Thus, we hope this article has provided valuable insights into Building a Password Game: A Comprehensive Guide to Engaging and Educational Entertainment. We appreciate your attention to our article. See you in our next article!