Securing Sensitive Data: A Guide to Creating Encrypted Folders
Related Articles: Securing Sensitive Data: A Guide to Creating Encrypted Folders
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to Securing Sensitive Data: A Guide to Creating Encrypted Folders. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Securing Sensitive Data: A Guide to Creating Encrypted Folders
In the digital age, safeguarding sensitive information is paramount. With the ever-present threat of unauthorized access, it is crucial to implement robust security measures to protect personal files, financial records, or any other data that requires confidentiality. One effective method for bolstering data security is by creating encrypted folders, effectively locking down the contents and restricting access to authorized individuals.
This comprehensive guide delves into the intricacies of creating encrypted folders, exploring various methods, outlining the underlying security principles, and highlighting the importance of this practice.
Understanding the Importance of Encrypted Folders
Encryption, the process of converting data into an unreadable format, plays a pivotal role in securing sensitive information. Encrypted folders leverage this technology to create a secure barrier around the data they contain. Without the appropriate decryption key, accessing the folder’s contents becomes impossible, effectively shielding sensitive information from unauthorized eyes.
The Benefits of Utilizing Encrypted Folders
-
Enhanced Data Security: Encryption renders the contents of the folder incomprehensible to anyone lacking the decryption key. This significantly reduces the risk of data breaches and unauthorized access, safeguarding sensitive information from prying eyes.
-
Compliance with Regulations: Many industries adhere to strict data privacy regulations, such as HIPAA for healthcare or GDPR for the European Union. Implementing encrypted folders can contribute to compliance with these regulations by providing an additional layer of security for sensitive data.
-
Protection Against Malware: Malicious software, such as ransomware, can encrypt files and demand payment for their release. Encrypted folders act as a deterrent, making it significantly more challenging for malware to access and encrypt the data within.
-
Peace of Mind: Knowing that your sensitive information is protected behind a secure barrier provides peace of mind, allowing you to focus on other tasks without worrying about data breaches or unauthorized access.
Methods for Creating Encrypted Folders
Several methods can be employed to create encrypted folders, each offering distinct advantages and disadvantages. Here are some of the most common approaches:
1. Operating System-Specific Tools:
-
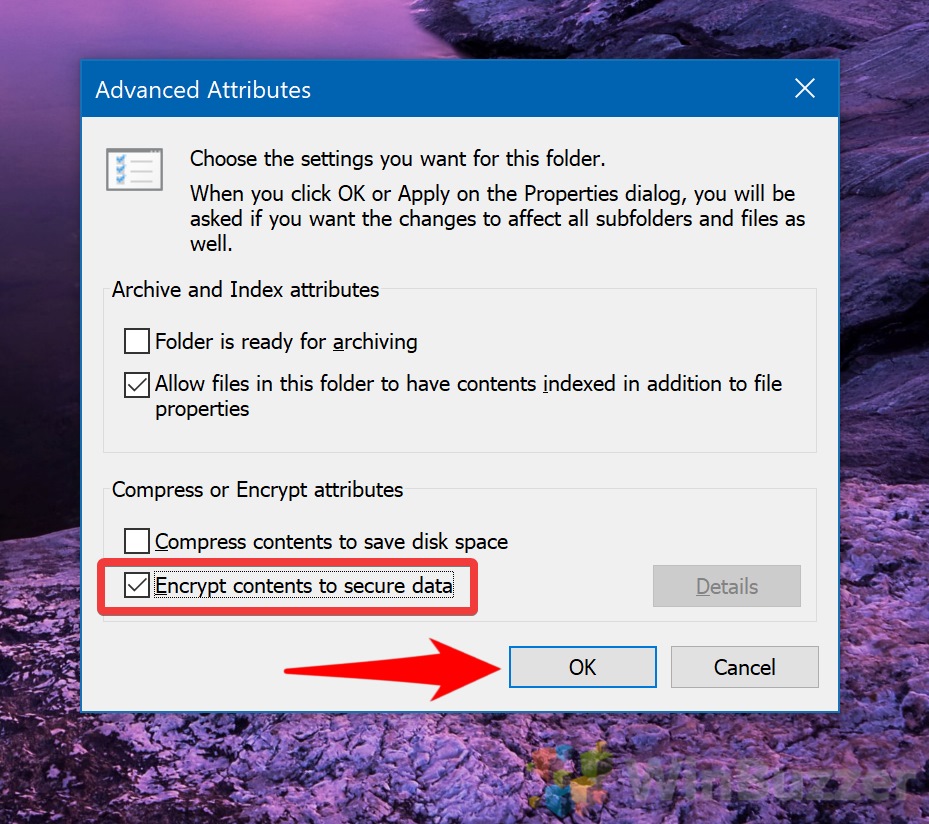
Windows: Windows offers built-in encryption capabilities through its File Explorer. Users can right-click on a folder, select "Properties," navigate to the "General" tab, and click "Advanced." From there, they can enable "Encrypt contents to secure data" to encrypt the folder and its contents.
-
macOS: macOS utilizes the "FileVault" feature for disk-level encryption. This encrypts the entire hard drive, including all folders and files. While providing comprehensive protection, it requires a password to access the system.
-
Linux: Many Linux distributions offer encryption tools like "cryptsetup" or "LUKS" for creating encrypted partitions or volumes. This method allows users to create a separate encrypted space within their file system, providing a secure location for sensitive data.
2. Third-Party Encryption Software:
-
VeraCrypt: A powerful and free open-source encryption software that allows users to create encrypted volumes or containers. These containers can be mounted as virtual drives, providing a secure space for storing sensitive data.
-
7-Zip: A popular archiving tool that supports encryption algorithms like AES-256 for securing compressed files. Users can create encrypted archives containing multiple files and folders, offering a convenient way to protect sensitive data.
-
AxCrypt: A user-friendly encryption software that allows users to create encrypted folders with a simple drag-and-drop interface. It supports cloud storage integration, enabling secure file sharing and collaboration.
3. Cloud Storage Providers:
-
Dropbox: Offers folder-level encryption for its paid plans, allowing users to create encrypted folders that remain protected even when shared with others.
-
Google Drive: Provides end-to-end encryption for files stored in its "Google Drive" service. This feature ensures that only the intended recipient can access the encrypted data.
-
Microsoft OneDrive: Offers a similar feature to Google Drive, allowing users to encrypt files and folders stored in their OneDrive account.
Choosing the Right Encryption Method
The choice of encryption method depends on individual needs and preferences. Consider the following factors:
-
Security Requirements: Determine the level of security required for your data. For sensitive information, consider using strong encryption algorithms like AES-256.
-
Ease of Use: Opt for methods that are user-friendly and intuitive, particularly if you are not tech-savvy.
-
Compatibility: Ensure the chosen method is compatible with your operating system, devices, and software.
-
Cost: Some encryption software may require paid subscriptions, while others are free and open-source.
Tips for Creating Secure Encrypted Folders
-
Use Strong Passwords: When creating encrypted folders, choose strong passwords that are difficult to guess. A strong password includes a combination of uppercase and lowercase letters, numbers, and symbols.
-
Enable Two-Factor Authentication: Whenever possible, enable two-factor authentication for your encryption software or cloud storage provider. This adds an extra layer of security by requiring a second authentication factor, such as a code sent to your phone or email.
-
Regularly Update Encryption Software: Keep your encryption software up-to-date with the latest security patches and updates to ensure that you are protected from the latest security threats.
-
Back Up Encrypted Data: Even with strong encryption, it is essential to back up your encrypted data regularly. This safeguards your data in case of hardware failure or accidental deletion.
-
Be Aware of Phishing Attacks: Be cautious of phishing emails or websites that may attempt to trick you into providing your encryption password or other sensitive information.
FAQs Regarding Encrypted Folders
1. Can I encrypt a folder on a shared network drive?
Yes, you can encrypt a folder on a shared network drive using third-party encryption software or by enabling file system encryption on the server hosting the network drive. However, ensure that the encryption method is compatible with the network drive’s operating system and security settings.
2. Is it safe to share encrypted folders with others?
Sharing encrypted folders with others requires careful consideration. Ensure that the recipient has the necessary decryption key to access the folder’s contents. If you are sharing the folder with multiple people, consider using a password manager to securely store and manage the decryption key.
3. Can I decrypt an encrypted folder without the password?
No, it is generally impossible to decrypt an encrypted folder without the correct password. If you forget your password, you may lose access to the folder’s contents.
4. How can I ensure that my encryption software is secure?
Choose reputable encryption software from trusted developers. Look for software that utilizes strong encryption algorithms, has a proven track record, and is regularly updated with security patches.
5. What are the best practices for managing encryption keys?
Store your encryption keys securely and separately from your encrypted data. Consider using a password manager to store your keys securely and manage them effectively.
Conclusion
Creating encrypted folders is a crucial step in safeguarding sensitive data in the digital age. By leveraging encryption technology, users can protect their files from unauthorized access, malware attacks, and data breaches. Choosing the right encryption method, employing strong passwords, and adhering to best practices for key management are essential for maximizing the security of encrypted folders. By implementing these measures, individuals and organizations can ensure the confidentiality and integrity of their sensitive data, fostering peace of mind and bolstering their digital security posture.





Closure
Thus, we hope this article has provided valuable insights into Securing Sensitive Data: A Guide to Creating Encrypted Folders. We appreciate your attention to our article. See you in our next article!